Configuring a Configurator Certificate
The Configurator certificate can be viewed, generated, or uploaded in the new Configurator screen (Settings > Administration > Configurator Certificates).
Operators view, download, or copy the currently loaded certificate by pressing the View Certificate button.
|
1.
|
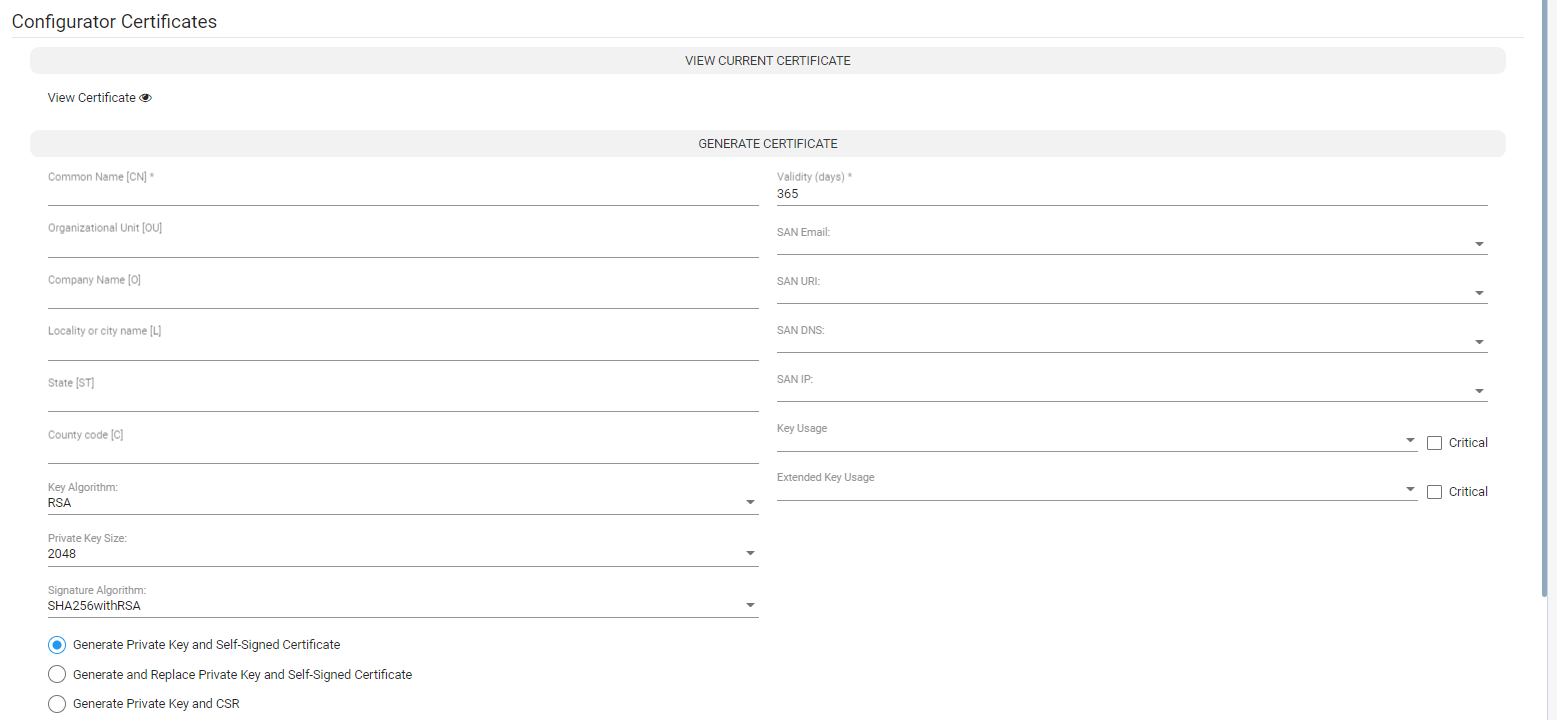
Open the Configurator Certificates screen (Settings > Administration > Configurator Certificates).
|
Configurator Certificates
|
2.
|
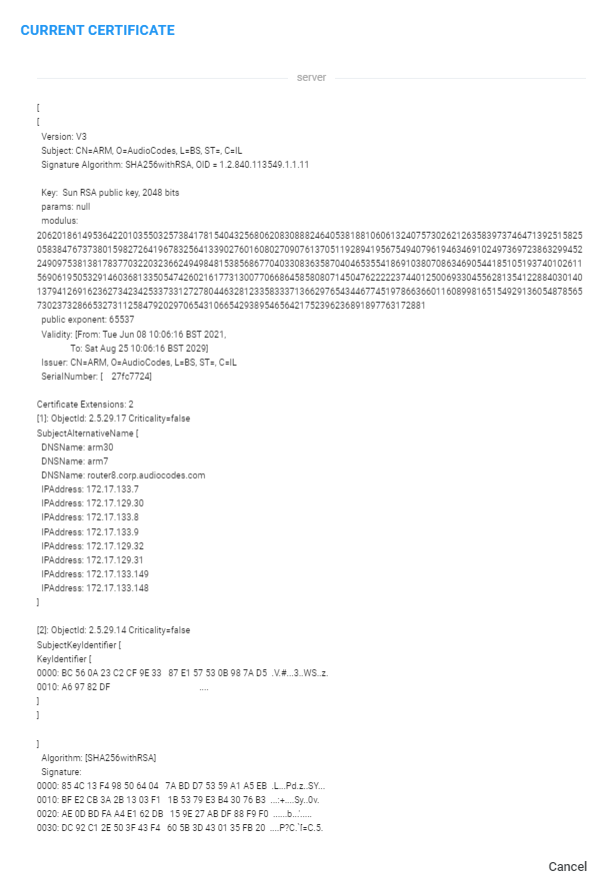
Click View Certificate.
|
Current Certificate
|
3.
|
Download or copy the PEM formatted certificate by pressing one of the icons in the Current Certificate view, as shown in the preceding figure. |
|
4.
|
Generate a self-signed certificate: In the Configurator Certificates page, select the Generate Private Key and Self-Signed Certificate option; you can generate and download a Java KeyStore (JKS) file which holds the private key and the self-signed certificate. This file can later be uploaded to the ARM as the Configurator or the Router certificate. |
|
5.
|
Configure the fields using the following descriptions as reference (common for all three operations): |
|
●
|
Common name. The only mandatory field. CN field of the certificate. Typically holds the server hostname or IP address. |
The following fields are optional; they typically hold information regarding the organization:
|
●
|
Organization unit, Company name, Locality or city name, State, Country code. |
|
●
|
Key Algorithm. Allows you to control whether the private / public key is RSA or EC (Elliptic curve); the default is RSA |
|
●
|
Private key size. Allows you to control the private key size. For RSA, one of the following values can be chosen: 2048, 3072, 4096. The default value is 2048. For EC, one of the following values can be chosen: 256, 384, or 521. The default is 256. |
|
●
|
Signature algorithm. Allows you to control the signature algorithm for RSA. One of the following can be chosen: SHA256-With-RSA, SHA384-With-RSA, or SHA512-With-RSA. The default is SHA256-With-RSA. For EC, one of the following can be chosen: SHA256-With-ECDSA, SHA384-With-ECDSA, or SHA512-With-ECDSA. The default value is SHA256-With-ECDSA. |
|
●
|
Validity. The number of days for which the certificate will be valid. The default value is 365. |
|
●
|
SAN (Subject Alternative Name) fields. As the common name can hold only one value, operators can use the SAN fields to reuse the certificate (while keeping it valid) for other hostnames (SAN DNS) or for other IP addresses (SAN IP). This option allows operators to create one certificate for the entire ARM network (Configurator and Routers) with valid hostnames and IP addresses. Other SAN fields can be used (though they are less useful for the ARM) such as Email and URI. |
|
●
|
Key Usage (KUEs). Allows you to control the purpose of the generated certificate to allow more tightly controlled usage of it. The following values can be used: |
|
◆
|
digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment, keyAgreement, keyCertSign, cRLSign, encipherOnly, and decipherOnly. |
|
●
|
Extended Key Usage (EKUs). An additional key usage option which operators can use to control serverAuth, clientAuth, codeSigning, emailProtection, timeStamping, OCSPSigning, or Empty. The default value is Empty, meaning the certificate can be used for any operation. |
Selecting a combination of Key Usage and Extended key usage can invalidate the Certificate for Server certificate purposes. In this case, the ARM will start up without TLS support.

